Scraps from various sources and my own writings on Digital, Artificial Intelligence, Disruption, Agile, Scrum, Kanban, Scaled Agile, XP, TDD, FDD, DevOps, Design Thinking, etc.
Page Hits
Wednesday, November 11, 2020
Friday, November 06, 2020
XSLT and XPath - W3Schools
- XSL (eXtensible Stylesheet Language) is a styling language for XML.
- XSLT stands for XSL Transformations.
- XSLT is a language for transforming XML documents.
- XPath is a language for navigating in XML documents.
- XQuery is a language for querying XML documents.
> Extensible Stylesheet Language
> CSS is the style sheet for HTML
> XLS is the stylesheet for XML (In fact it is more than a stylesheet)
XSL consists of four parts:
- XSLT - a language for transforming XML documents
- XPath - a language for navigating in XML documents
- XSL-FO - a language for formatting XML documents (discontinued in 2013)
- XQuery - a language for querying XML documents
- XSLT stands for XSL Transformations
- XSLT transforms an XML document into another XML document
- XSLT uses XPath to navigate in XML documents
Friday, September 04, 2020
Maven - Introduction / Maven.apache.org
Maven is a build automation tool used primarily for Java projects. Maven can also be used to build and manage projects written in C#, Ruby, Scala, and other languages. The Maven project is hosted by the Apache Software Foundation, where it was formerly part of the Jakarta Project. Wikipedia
Maven is a Java tool, so you must have Java installed in order to proceed.
Running this on Ubuntu, shows mvn is already installed. [This was installed because we ran this command previously
curl -O https://repo1.maven.org/maven2/com/microsoft/sqlserver/mssql-jdbc/8.4.0.jre14/mssql-jdbc-8.4.0.jre14.jar
abc@ubuntu:~/src/connector$ mvn --version
Apache Maven 3.5.2 (138edd61fd100ec658bfa2d307c43b76940a5d7d; 2017-10-18T18:58:13+11:00)
Maven home: /home/abc/bin/apache-maven-3.5.2
Java version: 14.0.1, vendor: Oracle Corporation
Java home: /home/abc/bin/jdk-14.0.1
Default locale: en_US, platform encoding: UTF-8
OS name: "linux", version: "5.4.0-45-generic", arch: "amd64", family: "unix"
Monday, August 31, 2020
Git command reference (Launchschool)
- git status Run this command any time and often to check on the status of the files in the git repository.
- git add This command stages changed files, readying them to be wrapped into the next commit.
- git commit This command commits staged files, wrapping them into a commit. A historical record of commits is what we refer to as a codebase's version or commit history.
- git log View the repository's commit history.
Tuesday, August 18, 2020
Monday, August 17, 2020
Java Refresher
- Byte = 8 bits
- Short - 16 bits
- Int - 32 bits
- Long - 64 bits
- Float - 32 bits (not precise, don't use for financials)
- Double - 64 bits - not very precise, don't use for financials.
- Char - 16 bits
- Boolean - True/ False
- Control + L = Clear Screen
JVM VS JRE VS JDK
Wednesday, August 12, 2020
Webservices (Guru99.com)
What is a Webservice?
- A web service is a software module that is designed to perform a certain set of tasks.
- It can be searched over the network (on the server where it it hosted) and invoked accordingly.
- The requests to the server are made thru REMOTE PROCEDURE CALLS (RPC).
- The main component of a web service is the data which is transferred between the client and server and is in XML format.
- So when applications talk to each other, they do in XML.
- Webservice uses a SOAP protocol for sending XML data in between the applications.
- Data is sent over in HTTP.
Why do you need a Webservice?
- Web services provide a common platform that allows multiple applications built on various programming languages (Java, .NET, Angular JS, Node.js, etc.) to have the ability to communicate with each other. (Don't have to bother in what language the front-end is written.)
Types of web services
- SOAP web services
- RESTful web services
Tuesday, August 11, 2020
Thursday, August 06, 2020
Inception meeting checklist
- Completed Design Kit (UI/UX) -fair understanding of the UI / UX
- Completed Architectural Design - fair understanding of the solution architecture
- Completed scoping document - scope clarity
- Ensure all stakeholders have been invited to the INCEPTION - confirm with the Product Owner
- Ensure all teams that are impacted in any way are iincluded in the inception - to align timelines
- Include the proposed agenda (topic - duration - speaker)
- Include any confluence links in the meeting invite to allow for preparation.
- Set-up Trello Board for story mapping session
- Set-up Ideaz Board to capture RAID/Parking Lot
- Confirm all presenters have accepted the invite and are aware they are to present
- Suggested inception agenda/format.
- Each Presentation should occur on a different day to allow time to absorb inception artefacts,
- keep each inception check-in efficient and mindful of everyone's time.
- Introductions
- Project Overview - Vision/Goals/Deliverables (Product Owner)
- Architectural Design Walk-thru (Project Architect)
- Design Kit Walk-thru (UI/UX Designer)
- RAID checkpoint (Risks, Assumptions, Issues, Decision, Parking Lot)
- Story Mapping Session
Wednesday, August 05, 2020
Tuesday, August 04, 2020
Friday, July 31, 2020
Serverless vs. PaaS vs. FaaS vs. BaaS (Blog.neap.co)
- Platform as a service
- Platform as a Service, allows you to focus on writing code without worrying about the underlying infrastructure. Beyond writing code, the only extra complexity might be around deployment and configuration (e.g., automatic scaling rules, geo-replication).
- Serverless
- Like PaaS, Serverless focuses on writing code without worrying about the underlying infrastructure, but it does it with even more deployment ease and less configuration.
- Overlaps PaaS and falls into the following two categories
- Function as a service
- Function as a service is a serverless product that hosts a piece of business logic (with usually a small footprint like resizing an image or sending an email). FaaS is well suited to build event-driven architecture.
- Backend as a service
- Backend as a service is a serverless backend ( e.g. DB hosting) that is a highly available backend that can be set up with barely any configuration and can scale almost infinitely. Once created, the developer focuses on deploying code or data only.
Evolution of Serverless
Microservices vs. API (Edureka)
Microservices
Monolithic Architecture
- Front end, back end, business logic all reside in a single code base.
- In case of a Microservice architecture, all the three functionalities - customer information, products available in cart and All the products available, can be put in three different services.
- Service A - Customer information
- Service B - Products available in cart
- Service C - All products available
- Composite Microservice - will take data from all the three services above and display it to the customer.
APIs
Where are APIs used in Microservices?
Summary
Wednesday, July 29, 2020
AZ-900 - Azure Fundamentals - Microsoft
What is Azure
- Azure is Microsoft's cloud platform.
- It is a continually expanding set of cloud services.
How does Azure Work?
- Space
- Energy
- Maintenance requirements
- If resources are left running after they are no longer needed, or created unauthorized.
- The solution is to use Azure's Resource Access Management.
Azure Services
- Compute services: performing calculations, executing logic, and running applicatinos.
- Virtual machines
- Containers
- Serverless computing including Microservices
- Cloud storage
- Disks attached to VM
- File shares
- Databases
- All these can expand or shrink as necessary
- Networking
- Let you set up private n/w conn to on-premise to Azure.
- App hosting
- Lets you run your entire web apps on a managed platform on Windows or Linux.
- The azure marketplace has a range of products including SAP, SQL, etc.
- Artificial Intelligence
- ML
- Pre-built cognitive services
- IOT
- Enables Integrate sensors and devices and manage with IOT hub, create dashboards, etc. to monitor and control.
- Integration
- Logic Apps
- Service Bus
- Connect applications and services, allows workflows to orchestrate business processes.
- Security
- Integrated into Azure
- Compute
- Networking
- Storage
- Mobile
- Databases
- Web
- IOT
- Big Data
- AI
- DevOps
Compute
Service name
|
Service function
|
Azure Virtual Machines
|
Windows or Linux virtual machines (VMs) hosted in Azure
|
Azure Virtual Machine Scale Sets
|
Scaling for Windows or Linux VMs hosted in Azure
|
Azure Kubernetes Service
|
Enables management of a cluster of VMs that run containerized services
|
Azure Service Fabric
|
Distributed systems platform. Runs in Azure or on-premises
|
Azure Batch
|
Managed service for parallel and high-performance computing
applications
|
Azure Container Instances
|
Run containerized apps on Azure without provisioning servers or VMs
|
Azure Functions
|
An event-driven, serverless compute service
|
Networking
TABLE 2
|
|
Service name
|
Service function
|
Azure Virtual Network
|
Connects VMs to incoming Virtual Private Network (VPN) connections
|
Azure Load Balancer
|
Balances inbound and outbound connections to applications or service
endpoints
|
Azure Application Gateway
|
Optimizes app server farm delivery while increasing application
security
|
Azure VPN Gateway
|
Accesses Azure Virtual Networks through high-performance VPN gateways
|
Azure DNS
|
Provides ultra-fast DNS responses and ultra-high domain availability
|
Azure Content Delivery Network
|
Delivers high-bandwidth content to customers globally
|
Azure DDoS Protection
|
Protects Azure-hosted applications from distributed denial of service
(DDOS) attacks
|
Azure Traffic Manager
|
Distributes network traffic across Azure regions worldwide
|
Azure ExpressRoute
|
Connects to Azure over high-bandwidth dedicated secure connections
|
Azure Network Watcher
|
Monitors and diagnoses network issues using scenario-based analysis
|
Azure Firewall
|
Implements high-security, high-availability firewall with unlimited
scalability
|
Azure Virtual WAN
|
Creates a unified wide area network (WAN), connecting local and remote
sites
|
Storage
Service name
|
Service function
|
Azure Blob storage
|
Storage service for very large objects, such as video files or bitmaps
|
Azure File storage
|
File shares that you can access and manage like a file server
|
Azure Queue storage
|
A data store for queuing and reliably delivering messages between
applications
|
Azure Table storage
|
A NoSQL store that hosts unstructured data independent of any schema
|
Mobile
- Azure enables devs to create mobile backend services for IOS, Android, and Windows.
- E.g. corporate sign-in, connecting to on premise resources such as SAP, oracle, sql, etc.
- Other features include
- Offline data sync
- Connectivity to on-premises data
- Broadcasting push notifications.
- Autoscaling to match business needs.
Databases
Service name
|
Service function
|
Azure Cosmos DB
|
Globally distributed database that supports NoSQL options
|
Azure SQL Database
|
Fully managed relational database with auto-scale, integral
intelligence, and robust security
|
Azure Database for MySQL
|
Fully managed and scalable MySQL relational database with high
availability and security
|
Azure Database for PostgreSQL
|
Fully managed and scalable PostgreSQL relational database with high
availability and security
|
SQL Server on VMs
|
Host enterprise SQL Server apps in the cloud
|
Azure Synapse Analytics
|
Fully managed data warehouse with integral security at every level of
scale at no extra cost
|
Azure Database Migration Service
|
Migrates your databases to the cloud with no application code changes
|
Azure Cache for Redis
|
Caches frequently used and static data to reduce data and application
latency
|
Azure Database for MariaDB
|
Fully managed and scalable MariaDB relational database with high
availability and security
|
Web
- Build and host web apps, and HTTP-based web services
Service Name
|
Description
|
Azure App Service
|
Quickly create powerful cloud web-based apps
|
Azure Notification Hubs
|
Send push notifications to any platform from any back end.
|
Azure API Management
|
Publish APIs to developers, partners, and employees securely and at
scale.
|
Azure Cognitive Search
|
Fully managed search as a service.
|
Web Apps feature of Azure App Service
|
Create and deploy mission-critical web apps at scale.
|
Azure SignalR Service
|
Add real-time web functionalities easily.
|
IOT
Service Name
|
Description
|
IoT Central
|
Fully-managed global IoT software as a service (SaaS) solution that
makes it easy to connect, monitor, and manage your IoT assets at scale
|
Azure IoT Hub
|
Messaging hub that provides secure communications between and
monitoring of millions of IoT devices
|
IoT Edge
|
Push your data analysis models directly onto your IoT devices,
allowing them to react quickly to state changes without needing to consult
cloud-based AI models.
|
Big Data
Service Name
|
Description
|
Azure Synapse Analytics
|
Run analytics at a massive scale using a cloud-based Enterprise Data
Warehouse (EDW) that leverages massive parallel processing (MPP) to run
complex queries quickly across petabytes of data
|
Azure HDInsight
|
Process massive amounts of data with managed clusters of Hadoop
clusters in the cloud
|
Azure Databricks
|
Collaborative Apache Spark–based analytics service that can be
integrated with other Big Data services in Azure.
|
AI
Service Name
|
Description
|
Azure Machine Learning Service
|
Cloud-based environment you can use to develop, train, test, deploy,
manage, and track machine learning models. It can auto-generate a model and
auto-tune it for you. It will let you start training on your local machine,
and then scale out to the cloud
|
Azure Machine Learning Studio
|
Collaborative, drag-and-drop visual workspace where you can build,
test, and deploy machine learning solutions using pre-built machine learning
algorithms and data-handling modules
|
Service Name
|
Description
|
Vision
|
Image-processing algorithms to smartly identify, caption, index, and
moderate your pictures and videos.
|
Speech
|
Convert spoken audio into text, use voice for verification, or add
speaker recognition to your app.
|
Knowledge mapping
|
Map complex information and data in order to solve tasks such as
intelligent recommendations and semantic search.
|
Bing Search
|
Add Bing Search APIs to your apps and harness the ability to comb
billions of webpages, images, videos, and news with a single API call.
|
Natural Language processing
|
Allow your apps to process natural language with pre-built scripts,
evaluate sentiment and learn how to recognize what users want.
|
DevOps
Service Name
|
Description
|
Azure DevOps
|
Azure DevOps Services (formerly known as Visual Studio Team Services,
or VSTS), provides development collaboration tools including high-performance
pipelines, free private Git repositories, configurable Kanban boards, and
extensive automated and cloud-based load testing
|
Azure DevTest Labs
|
Quickly create on-demand Windows and Linux environments you can use to
test or demo your applications directly from your deployment pipelines
|
Azure Data Centre and Regions
- Azure is made up of data centres around the world.
- When you are using a resource such as a SQL db or virtual machine, you are using an equipment at one of these locations.
- Azure organizes these data centres into REGIONS.
- A region is a geographical area on the planet containing at least one, but potentially multiple datacenters that are nearby and networked together with a low-latency network. Azure intelligently assigns and controls the resources within each region to ensure workloads are appropriately balanced.
- Some resources are available in only some REGIONS.
- Azure regions give the flexibility of bringing applications closer to your users.
Azure Geographies
- Americas
- Europe
- Asia Pacific
- Middle East and Africa
Availability Zones
- Availability Zones are physically separate datacenters within an Azure region.
- Each availability zone is made up of one ore more data centres.
- If one goes down, the other continues working.
- Central US
- East US 2
- West US 2
- West Europe
- France Central
- North Europe
- Southeast Asia
Region Pairs
- If there is an extensive outage, on region out of every pair is prioritized for restoration.
- Updates are planned one region at time (out of a pair) to minimize downtime and risk of application outage.
- Data continues to reside in its pair for tax & law jurisdiction purposes.
Summary -- geography, region pairs
Azure Regional Pairs
| Geography | Regional Pair A | Regional Pair B |
|---|---|---|
| Asia-Pacific | East Asia (Hong Kong) | Southeast Asia (Singapore) |
| Australia | Australia East | Australia Southeast |
| Australia | Australia Central | Australia Central 2 |
Azure SLAs
- Performance Targets
- Are specific to each Azure product or service.
- Uptime and connectivity guarantees
- Ranges from 3 9's (99.9%) to 5 9's (99.999%) - first figure below.
- Azure thru SLAs, describes how MS will respond to product or service fails by giving service credits.
- Cust may have a discount applied on their bill as a compensation for under performance.
Composite SLAs
- The resultant SLA by combining SLAs is called a composite SLA.
- With this design, the application is still available even if DB fails.
- The application fails only if both DB and Queue fail simultaneously.
- Adding Queue to the web app, the composite SLA is
- Failure % for SQL DB is 100% - 99.99% = 0.01% which is 0.01/100 = 0.0001
- Failure % for Queue is 100% - 99.9% = 0.1% which is 0.1/100 = 0.001
- Joint probability of failure for SQL DB and Queue is 0.0001 X 0.001 = 0.0000001
- Probability of up time for Either SLQ DB OR Queue = 1- 0.0000001 = 99.99999%
- So, Either SQL DB OR Queue is 99.9999%.
- Composite SLA is therefore 99.95% X 99.99999 = 99.95%
Resiliency
- Architecture needs to be designed for resiliency
- Perform FMEA - Failure Mode Effect Analysis for infra when designing.
- If Application SLA is 4 9's, then the Azure solution must be self-diagnosing and self-healing (can't be manual to achieve the target).
- SLA performance targets above 4 9's are difficult to achieve.
Azure Management
- Azure portal - to interact with Azure via a GUI
- Azure PowerShell / Azure command line - command line, automation based interactions with Azure.
- Azure Cloud Shell - Web-based CLI
- Azure Mobile App - for monitoring and managing your resources from your mobile device.
Azure Advisor
- Get proactive, actionable, and personalized best practice recommendations.
- Improve the performance, security, and high availability of your resources as you identify opportunities to reduce your overall Azure costs.
- Get recommendations with proposed actions inline.
Azure Portal Dashboards
Azure New Features
- Azure New Features >> first available for beta testing and other pre-release features >> released to customers as part of Azure Default product set (called General Availability).
- Private preview - for specific customers
- Public preview - for all customers
Azure Compute
Azure Virtual Machines
- During testing and development
- When running applications in the cloud
- When extending your data centre to the cloud.
- During disaster recovery
- Is a logical grouping of two or more VMs
- VM pairs as part of the availability set are in different update domains so that there is least impact during planned maintenance. Update domains indicate groups of VMs and underlying physical hardware that can be rebooted at the same time. Update domains are a logical part of each data center and are implemented with software and logic.
- During unplanned events, VMs failover to a working physical server.
- Fault Domain -- group of VMs that share common hardware are in the same fault domain. A fault domain is essential a rack of servers.
- Starts a pool of compute VMs for you
- Installs applications and staging data
- Runs jobs with as many tasks as you have
- Identifies failures
- Requeues work
- Scales down the pool as work completes
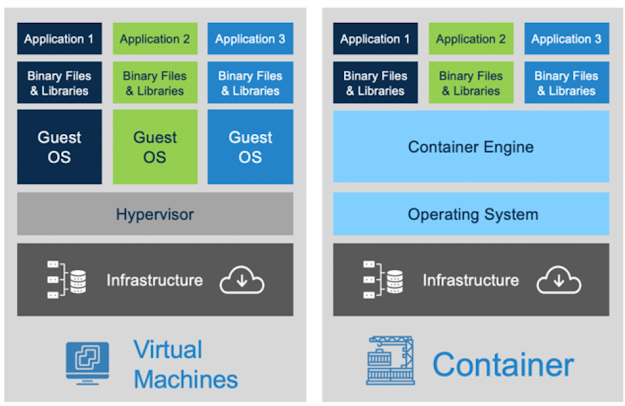
AZURE Containers
- A container is a modified Runtime Environment built on top a host OS that executes your application.
- Run multiple instances of application on a single host machine.
- Can run multiple OS.
- Container orchestrator can start, stop, and scale out application instances.
- Containers are lighter than VMs.
- Can run multiple isolated application on a single container host.
- Containerized apps are smaller in size.
- Apps are quicker to launch.
- Dev process is simplified cos dev is similar to prod.
- If you want complete control of the environment, choose VM, if you want portability, and performance go for containers.
- VMs provide an abstraction layer for CPU, MEM and storage.
- VMs run only one OS at a atime.
- VMs virtualise the h/w while Containers virtualise OS.
- Azure Container Instances (ACI) - is a PaaS offering that allows you to upload your containers and execute them directly with automatic elastic scale.
- Azure Kubernetes Service (AKS) - Azure Kubernetes Service (AKS) is a complete orchestration service for containers with distributed architectures with multiple containers.
Migrating Apps to Containers
- You convert an existing application to one or more containers and then publish one or more container images to the Azure Container Registry.
- By using the Azure portal or the command line, you deploy the containers to an AKS cluster.
- Azure AD controls access to AKS resources.
- You access SLA-backed Azure services, such as Azure Database for MySQL, via OSBA.
- Optionally, AKS is deployed with a virtual network.
Azure App Service
- Web Apps - full support for hosting web apps using ASP.NET, ASP.NET Core, Java, Ruby, Node.js, PHP, or Python. You can choose either Windows or Linux as the host operating system.
- API Apps - you can build REST-based Web APIs using your choice of language and framework. You get full Swagger support, and the ability to package and publish your API in the Azure Marketplace.
- WebJobs - WebJobs allows you to run a program (.exe, Java, PHP, Python, or Node.js) or script (.cmd, .bat, PowerShell, or Bash) in the same context as a web app, API app, or mobile app. They can be scheduled, or run by a trigger. WebJobs are often used to run background.
- Mobile Apps - You can use this to quickly build a back-end for iOS and Android apps. With just a few clicks in the Azure portal you can:
- Store mobile app data in a cloud-based SQL database
- Authenticate customers against common social providers such as MSA, Google, Twitter, and Facebook
- Send push notifications
- Execute custom back-end logic in C# or Node.js
Azure Serverless Computing
- Serverless computing is the abstraction of servers, infrastructure, and OSs.
- Azure takes care of managing the server infrastructure and allocation/deallocation of resources based on demand.
- Abstraction of servers
- Serverless computing abstracts the servers you run on. You never explicitly reserve server instances; the platform manages it for you. Each function execution can run on different compute instance and this execution is transparent to the code. With this arch, you worry only about deploying code which then runs with high availability.
- Event driven scale
- Instead of writing an entire application, the developer writes a function which contains both code and meta data about its triggers and bindings.
- Serverless computing responds to incoming triggers / events (e.g. a function runs everyday at 10:00 am UTC, etc.).
- The platform automatically schedules the function to run based on the trigger / event and scales the number of compute instances based on the rate of coming events.
- Trigger defines how the function is invoked.
- Bindings provide ways to connect services from within the code.
- Micro billing
- Even if a customer's website gets only one hit a day, they still pay for a full day's worth of availability. With serverless computing, they pay only for the time their code runs.
- For example, if the code runs once a day for two minutes, they're charged for one execution and two minutes of computing time.
- Azure functions:
- Azure Logic Apps:
- Detect the intent of the message with cognitive services
- Create an item in SharePoint to track the issue
- If the customer isn't in your database, add them to your Dynamics 365 CRM system
- Send a follow-up email to acknowledge their request
Functions vs. Logic Apps
Azure Data Storage
- Automated backup and recovery
- Replication across globe
- Support for data analytics
- Encryption capabilities
- Multiple data types (video, text, binary etc.)
- Data storage in virtual disks - 32TB in virtual disks.
- Storage tiers prioritise access to data based on frequently used vs. rarely used information.
- Structure data
- Structured data is data that adheres to a schema, so all of the data has the same fields or properties. Structured data can be stored in a database table with rows and columns.
- Semi structured data
- Semi structured data does not fit into tables, rows and columns. Use tags and keys. Semi structured data is also referred to as non-relational or NoSQL data.
- Unstructured data
- BLOB - PDF, JPG, JSON, video content, etc.
Azure SQL Database
- Azure SQL Database is a relational database as a service (DaaS) based on the latest stable version of the Microsoft SQL Server database engine.
Azure Cosmos DB
Azure BLOB Storage
Azure Datalake
Azure Files
Azure Queue
Disk Storage
Storage Tiers
- Hot Storage Tier
- Optimised for storing data that is accessed frequently.
- Cool Storage Tier
- Optimised for data that is infrequently accessed and stored for at least 30 days.
- Archive Storage Tier
- For data that is rarely accessed and stored for at least 180 days with flexible latency requirements.
Encryption
- SSE - Azure storage service encryption for data at rest.
- Secure data to meet org security and regulatory requirements.
- Encrypts data before storing, de-crypts before returning.
- Encryption and decryption transparent to user.
- Client side encryption
- Data is already encrypted by client libraries.
- Azure stores this data (encrypted state at rest).
- During retrieval, this data is decrypted
Replication
- Replication type is created when storage account is created.
- Replication feature ensures data is durable and always available
- Azure provides regional and geographic replication (protect against natural disasters, etc.).
Azure Data Storage vs. On-premises Data Storage
Loosely coupled Architecture
Azure Region
Azure Virtual Network
Azure Network Security Group
Azure Load Balancer
- Availability refers to how long a service is up.
- High availability refers to a service that has been running for a long period of time.
- Systems ability to stay operational during abnormal conditions
- Distribute traffic evenly among systems in a pool.
- Load balancer helps achieve both high availability and resiliency.
Azure Application Gateway
- Cookie affinity - store cookies on the same backend server.
- SSL termination - manages SSL certificates and pass unencrypted traffic to backend servers to avoid encryption / decryption overhead.
- Web application firewall - Supports a sophisticated WAF firewall with detailed monitoring, logging etc.
- URL rule based routes - allows to route traffic based on URL patterns.
- Rewrite HTTP headers - You can add / remove information from inbound and outbound HTTP headers, for security scenarios.
Azure DNS
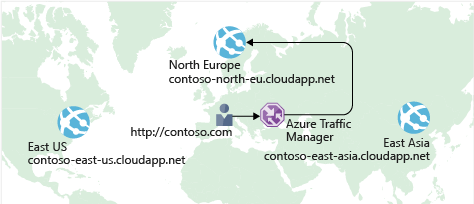
Azure Traffic Manager
Load Balancer vs. Traffic Manager
Security and Trust in Azure / Cloud Security
- IAAS - Microsoft provides VMs and virtual networks. However, it is
- Our responsibility for patch management and secure OS and s/w.
- Our responsibility to configure n/w and be secure.
- PAAS - Azure is taking care of OS and foundational s/w like DB.
- Security patches etc. taken care by Azure.
- SAAS
- With SAAS we outsource everything to Azure.
Layered approach to Security
Azure Security Centre
- Provide security recommendations based on configurations, etc.
- Monitor security settings for unauthorised change.
- Apply new security settings for new resources as they come online.
- Continuous monitoring of all services
- Use machine learning to detect and block malware.
- Analyse and identify inbound attacks.
- Provide just in time access controls for ports.
Identity and Access
- Is a cloud-based identity service.
- Built in support for synchronising with existing on-premise AD.
- Provides authentication.
- Provides SSO.
- Multi factor authentication - allows increased security of identity.
- Something you know (for example a password)
- Something you possess (for example a mobile - an SMS on mobile).
- Something you are (for example, biometry)
- Provides identities to services thru Service Principles
- Identity -- Identity is a thing like a person with password or a service / servers that can be authenticated.
- Principal is an Identity with a certain roles or claims. Identity and principal go together.
- User Principal -- an identity used by a person.
- Service Principal -- is an identity that is used by a service or application. And like other identities, it can be assigned roles.
- Managed Identities make the task of maintaining service principals easier.
- There is a service that wants to authenticate.
- You create a managed identity on your org's active directory.
- Azure infra automatically takes care of authenticating this service and managing the account.
- Use this account like any other Azure AD account including allowing the authenticated service secure access to resources.
- close example document upload service uses an authentication to upload docs in SAP in Sony Basingstoke,
Role based access control
Privileged Identity Management
Encryption
Encryption on Azure
- Encrypt raw storage
- Azure storage service encrypts data at rest
- Azure storage service encrypts virtual machine disks
- Azure disk encryption service is a capability that allows encryption of Windows, Linux IAAS VMs. (Uses Bitlocker)
- Encrypt databases
- Transcription Data Encryption (TDE) helps protect Azure SQL DB and Azure DW against malicious activities.
- TDE encrypts the storage of an entire database by using a symmetric key called the database encryption key.
- Encrypt secrets
- Azure Key Vault
- Azure Key Vault is a centralised cloud service for storing your application secrets. Key Vault helps you control your applications' secrets by keeping them in a single, central location and by providing secure access, permissions control, and access logging capabilities.
- Secrets management
- Key management (encryption of keys)
- Certificate management.
- Store secrets backed by hardware security modules (HSMs)
Azure Certificates
- Service Certificates
- Are used for cloud services and allow secure communication from and to the service.
- Management Certificates
- Are used for authenticating with the management API
- Are used to authenticate with the classic deployment model.
- Many programs and tools (such as Visual Studio or the Azure SDK) use these certificates to automate configuration and deployment of various Azure services. However, these types of certificates are not related to cloud services.
Azure Key Vault with Certificates
Network Security
- Azure has layered security approach to network ( see above sections)
- Azure firewall
- Is a managed, cloud based, network security service that protects Azure virtual network resources.
- Protection for HTTPS, RDP ,SSH, FTP protocols
- Azure application gateway
- Is a load balancer that includes a Web application firewall (WAF) that provides protection from common, known vulnerabilities.
- Network Virtual Appliances (NVA) are ideal options for non-HTTP services.
DDoS - Distributed Denial of Services Attacks
- Basic - Is automatically enabled as part of Azure platform.
- Standard - additional mitigation capabilities.
- Volumetric attacks
- Protocol attacks
- Resource layer attacks
Protecting Shared Documents - AIP / Azure Information Protection
Azure ATP - Advanced Threat Protection
Microsoft Security Development Lifecycle (SDL)
Infrastructure Standards with Azure Policy
- Azure lets you set up policies for cloud infra and these policies will enforce rules for the created resources thus ensuring compliance with corporate standards, SLAs, etc.
- Azure Policy is an Azure service you use to create, assign and, manage policies. These policies enforce different rules and effects over your resources so that those resources stay compliant with your corporate standards and service level agreements.
- Example -- Imagine we allow anyone in our organization to create virtual machines (VMs). We want to control costs, so the administrator of our Azure tenant defines a policy that prohibits the creation of any VM with more than 4 CPUs. Once the policy is implemented, Azure Policy will stop anyone from creating a new VM outside the list of allowed stock keeping units (SKUs).
- Any VM you add will be checked by policy.
- Azure policy will audit all existing VMs.
- Azure Policy is DIFFERENT FROM RBAC (Role based access control).
- Both Azure policy and RBAC go hand in hand to ensure organisational business rules are applied.
- RBAC
- Manages who has access to Azure resources, what areas they have access to, and what they can do with those resources.
- Example, allow users to access and manage VMs, websites, etc.
- Azure Policy
- Focus on resource properties during deployment and for already existing resources.
- Example, policy to ensure users can only deploy DS series of VMs.
- Create policy definition --
- tells what to evaluate and what action to take.
- Represented by a .JSON file.
- Assign a definition to a scope of resources. (Apply policy)
- You can assign any of these policies through the Azure portal, PowerShell, or Azure CLI. When you assign a policy definition, you will need to supply any parameters that are defined.
- View policy evaluation results
- Use the Azure portal and the applied policies to identify non compliant resources.
Azure Initiatives
|
Policy definition |
Purpose |
|
Monitor unencrypted SQL Database in Security Center |
For monitoring unencrypted SQL databases and servers. |
|
Monitor OS vulnerabilities in Security Center |
For monitoring servers that do not satisfy the configured baseline. |
|
Monitor missing Endpoint Protection in Security Center |
For monitoring servers without an installed endpoint protection agent. |
Azure Management Group
Azure Blueprints
Azure Compliance Manager
- Compliance manager makes it easy to perform risk assessments of Microsoft's cloud services.
- Use it to manage your organisation's compliance activities from implementation to reporting.
- There are four sources as below:
- Microsoft Privacy Statement
- The Microsoft privacy statement explains what personal data Microsoft processes, how Microsoft processes it, and for what purposes.
- MS Trust Centre
- Trust Center is a website resource containing information and details about how Microsoft implements and supports security, privacy, compliance, and transparency in all Microsoft cloud products and services.
- Service Trust Portal
- Is a companion feature of Trust Centre
- The Service Trust Portal (STP) hosts the Compliance Manager service, and is the Microsoft public site for publishing audit reports and other compliance-related information relevant to Microsoft's cloud services. STP users can download audit reports produced by external auditors and gain insight from Microsoft-authored reports that provide details on how Microsoft builds and operates its cloud services.
- These compliances
- ISO
- SOC
- NIST
- FedRAMP
- GDPR
- STP allows you to:
- Access audit reports on a single page
- Access compliance guides
- Access trust documents
- Compliance Manager
- Compliance manager is a workflow-based risk assessment dashboard within Service Trust Portal that enables you to track, assign, and verify your organisation's regulatory compliance activities related to Microsoft professional services and Microsoft cloud services such as Office 365, Dynamics 365, and Azure.
- Enables to assign, track and record compliance assessment related activities.
- Provides compliance score.
- Provides a secure repository in which to upload and manage evidence and other artifacts related to compliance activities.
- Produces richly detailed reports in Microsoft Excel that document the compliance activities.
- Provides recommended actions you can take to improve regulatory compliance.
Monitor Service Health
- Azure monitor
- Azure Monitor maximizes the availability and performance of your applications by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments. It helps you understand how your applications are performing and proactively identifies issues affecting them and the resources they depend on.
- Data sources: Azure monitor collects data from various sources...
- Diagnostics
- Getting Application Data
Azure Resources Manager
Create Policy
RBAC
Resource Locks
- subscriptions,
- resource groups, and
- to individual resources, and are inherited when applied at higher levels.
Purchasing Azure Products and Services
- Azure products and services are arranged by category.
Salesforce Platform Basics - Trailhead
https://trailhead.salesforce.com/content/learn/modules/starting_force_com Salesforce Platform Basics Customer Relationship Management (CRM...
-
Requirements Analysis -- Business requirements document or business requirements specification System Design -- Systems requireme...